Bitcoin Miner server
A few years ago, cryptocoin mining was a popular pastime. Cryptocurrencies work by making participants perform huge numbers of cryptographic calculations until they get lucky and “mine” a coin. The more computers you could call upon, the better your chance of paydirt.
So, numerous threats appeared that used infected computers to mine cryptocurrencies at the expense of the victim. Mining coins can burn through a lot of electricity to power the computers in use, so infecting someone else’s computer provided the attacker with free CPU resources from each infected system, which would deliver any rewards from the mining operations into the attacker’s wallet.
It was an obvious gambit for the crooks, but after a while the average PC was no longer enough to mine a cryptocurrency like Bitcoin, because the Bitcoin system deliberately increases the difficulty of mining over time, to prevent the supply of Bitcoins from expanding indefinitely.
But newer cryptocurrencies offer legitimate participants to get in “on the ground floor, ” as it were, making them a viable target once again for cryptomining crooks.
In this paper, Marosi dives into how Mal/Miner-C quietly infects victims’ computers and communicates with host servers to run mining operations covertly in the background. Alone, one computer may not make a big impact on cryptocurrency mining, but the criminals aim to infect as many computers as possible with their malware (which has worm-like self-replicating properties) so they can reap the cumulative financial reward from hundreds of thousands of infected computers.
During the course of his research, Marosi found that a specific kind of Seagate product, the Seagate Central Network Attached Storage (NAS), turned up surprisingly commonly as a distribution server for Mal/Miner-C malware, even though the malware itself can’t run on a Seagate Central device.
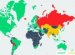
Marosi decided to dig further, and scanned the globe looking for Seagate Central. More than 7, 000 of the servers he found had inadvertently been connected to the internet so that literally anyone in the world could write to them. Of those, more than 70% had already been co-opted by the crooks into what was effectively a free content delivery network for their malware.